Your Fingerprint Can Be Hacked For $5. Here’s How. - Kraken Blog
date
May 27, 2022
slug
指纹破解
status
Published
summary
指纹 Hack
tags
安全
type
Post

Fingerprint authentication is a convenient alternative to passwords and PIN codes. Who wants to spend time typing in a lengthy string of numbers, letters and characters when a simple tap will suffice?
Unfortunately, that convenience comes at a cost. Because, unlike a regular password, you leave your fingerprint on taxi doors, iPhone screens, and glasses of wine at your local restaurant.
In this article, the Kraken Security Labs Team demonstrates just how easy it is for malicious actors to bypass your favorite login method.
Stealing the Fingerprint
To compromise your device or account, we don’t even need direct access to your fingerprint. A photo of a surface you’ve touched (from a table at the local library to the equipment at your nearest gym) will do.

A photo of a victim’s fingerprint on their computer screen.
With this photo at our disposal, an hour in Photoshop yields a decent negative:
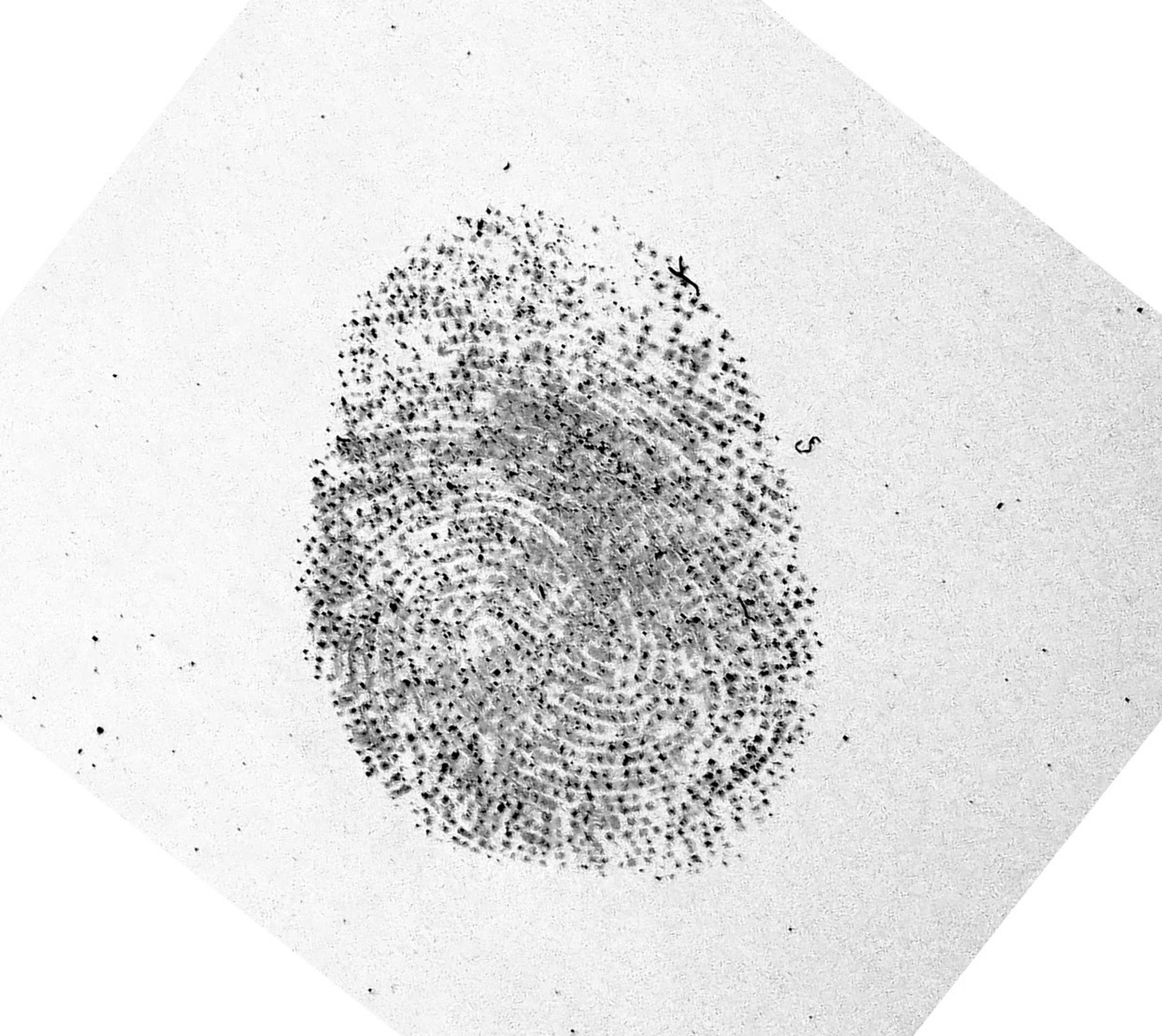
The negative of the fingerprint from the previous photo.
Next, we’ll print the image onto an acetate sheet with a laser printer — the toner creates a 3D structure of the fingerprint on the sheet.

The acetate sheet with our fresh print.
For our final step, we add some wood glue on top of the print to bring to life a fake fingerprint that we can use on a scanner.

Building the synthetic fingerprint.
Launching the Attack
With the fingerprint in hand, all we need to do is place it on the scanner.
Our fingerprint working on a MacBook Pro.
We were able to perform this well-known attack on the majority of devices our team had available for testing. Had this been a real attack, we would have had access to a vast range of sensitive information.
Protecting Yourself From the Attack
A fingerprint should not be considered a secure alternative to a strong password. Doing so leaves your information — and, potentially, your cryptoassets — vulnerable to even the most unsophisticated of attackers.
It should be clear by now that, while your fingerprint is unique to you, it can still be exploited with relative ease. At best, you should only consider using it as second-factor authentication (2FA).
Want to up your security hygiene? Be sure to check out our Support Center guides for other tips on avoiding common security pitfalls.