bitwarden设立一个备份镜像网站
date
May 9, 2022
slug
tip-bitwarden-duplicate-sync
status
Published
summary
一旦源站蹦了,马上改个域名就可以用上了
tags
tip
type
Post
URL
Problem & SummarySolutionA站 - 源B站 - 副本 准备使用docker-compose.yml直接使用docker with ssl用 https://domain:8443来访问如何和npm_nginx_proxy_manager 一起用反向代理配置
Problem & Summary
- 做到使用 bitwarden.a.com 和 bitwarden.b.com 保持每3小时的sync
Solution
A站 - 源
ssh-keygen -t ecdsa -b 521
# 把 ~/.ssh/id_ecdsa.pub 添加到B站的 ~/.ssh/authorized_keys
crontab -e
# uchk2m ucloud -> 20231101
21 */3 * * * /usr/bin/rsync -e 'ssh -p 22022' -ahzP --delete /data/bitwarden/data/ root@bitwarden9527.nn.com:/data/bitwarden/data/ && ssh -p 22022 root@bitwarden9527.nn.com 'cd /data/bitwarden && docker-compose down && docker-compose up -d;'
# uchk2m ucloud -> 20231101 45.43 - for composer
21 */3 * * * /usr/bin/rsync -e 'ssh -p 22022' -ahzP --delete /data/bitwarden/data/ root@xxx.xxx.xxx:/data/bitwarden/data/ && ssh -p 22022 root@xxx.xxx.xxx 'cd /data/bitwarden && docker-compose down && docker-compose up -d'
# bwh4 206.190 - for direct docker
21 */3 * * * /usr/bin/rsync -e 'ssh -p 22022' -ahzP --delete /data/bitwarden/data/ root@yyy.yyy.yyy:/data/bitwarden/data/ && ssh -p 22022 root@yyy.yyy.yyy 'docker restart bitwarden_ssl'
B站 - 副本
准备
mkdir -p /data/bitwarden && cd /data/bitwarden
BITWARDEN_ADMIN_TOKEN='XB3738v2'
BITWARDEN_YUBICO_CLIENT_ID=663
BITWARDEN_YUBICO_SECRET_KEY=ImiWwx
BITWARDEN_DOMAIN=‘https://bitwarden.b.com'使用docker-compose.yml
cat > docker-compose.yml <<EOF
version: '3'
services:
vaultwarden:
image: vaultwarden/server:latest
container_name: bitwarden
restart: always
environment:
- WEBSOCKET_ENABLED=true # Enable WebSocket notifications.
- SIGNUPS_ALLOWED=true
- WEB_VAULT_ENABLED=true
- ADMIN_TOKEN=$BITWARDEN_ADMIN_TOKEN
- YUBICO_CLIENT_ID=$BITWARDEN_YUBICO_CLIENT_ID
- YUBICO_SECRET_KEY=$BITWARDEN_YUBICO_SECRET_KEY
volumes:
- ./data:/data
caddy:
image: caddy:2
container_name: caddy
restart: always
ports:
- 80:80 # Needed for the ACME HTTP-01 challenge.
- 443:443
volumes:
- ./Caddyfile:/etc/caddy/Caddyfile:ro
- ./caddy-config:/config
- ./caddy-data:/data
environment:
- DOMAIN=$BITWARDEN_DOMAIN # Your domain.
- EMAIL=xxx@disroot.org # The email address to use for ACME registration.
- LOG_FILE=/data/access.log
EOF
cat > Caddyfile <<EOF
{\$DOMAIN}:443 {
log {
level INFO
output file {\$LOG_FILE} {
roll_size 10MB
roll_keep 10
}
}
# Use the ACME HTTP-01 challenge to get a cert for the configured domain.
tls {\$EMAIL}
# This setting may have compatibility issues with some browsers
# (e.g., attachment downloading on Firefox). Try disabling this
# if you encounter issues.
encode gzip
# Notifications redirected to the WebSocket server
reverse_proxy /notifications/hub vaultwarden:3012
# Proxy everything else to Rocket
reverse_proxy vaultwarden:80 {
# Send the true remote IP to Rocket, so that vaultwarden can put this in the
# log, so that fail2ban can ban the correct IP.
header_up X-Real-IP {remote_host}
}
}
EOF
docker-compose up -d
sleep 1s; docker-compose logs -f直接使用docker with ssl
# 实现准备好CloudFlare上面生成好的 key + cert,保15年
# 但必须是Full SSL
# Proxy 小云朵要打上
docker run -d \
--name bitwarden \
--restart=always \
-p 8443:80 \
-e SIGNUPS_ALLOWED=true \
-e ADMIN_TOKEN=$BITWARDEN_ADMIN_TOKEN \
-e WEB_VAULT_ENABLED=true \
-e WEBSOCKET_ENABLED=true \
-e YUBICO_CLIENT_ID=$BITWARDEN_YUBICO_CLIENT_ID \
-e YUBICO_SECRET_KEY=$BITWARDEN_YUBICO_SECRET_KEY \
-e ROCKET_TLS='{certs="/ssl/certs.pem",key="/ssl/key.pem"}' \
-v /data/bitwarden/ssl:/ssl \
-v /data/bitwarden/data:/data \
vaultwarden/server:latest
sleep 1; docker logs -f bitwarden
用 https://domain:8443来访问
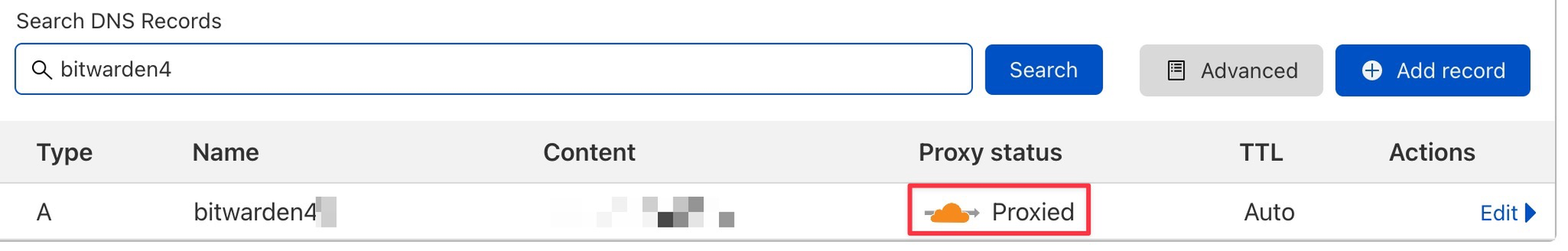
如何和npm_nginx_proxy_manager 一起用
cat > docker-compose.yml <<EOF
version: '3'
services:
vaultwarden:
image: vaultwarden/server:latest
container_name: bitwarden
restart: always
#ports:
# - 18380:80 # default is 80
# - 18383:443
environment:
- WEBSOCKET_ENABLED=true # Enable WebSocket notifications.
- SIGNUPS_ALLOWED=true
- WEB_VAULT_ENABLED=true
- ADMIN_TOKEN=$BITWARDEN_ADMIN_TOKEN
- YUBICO_CLIENT_ID=$BITWARDEN_YUBICO_CLIENT_ID
- YUBICO_SECRET_KEY=$BITWARDEN_YUBICO_SECRET_KEY
volumes:
- ./data:/data
networks:
default:
name: npm_nginx_proxy_manager-network
external: true
EOF反向代理配置
#PROXY-START/
location / {
proxy_pass http://bitwarden:80;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header REMOTE-HOST $remote_addr;
add_header X-Cache $upstream_cache_status;
#Set Nginx Cache
add_header Cache-Control no-cache;
expires 12h;
}
location /notifications/hub {
proxy_pass http://bitwarden:3012;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
}
location /notifications/hub/negotiate {
proxy_pass http://bitwarden:80;
}
#PROXY-END/